The Australian Cyber Security Centre has issued a warning about Bulletproof Hosting Providers (BPH), which play a central role in…
Researchers uncovered a critical security vulnerability in Rails applications that leverages the Bootsnap caching library. This exploit allows attackers to achieve…
Anonymous tinkerer claims to have bypassed an AI assistant’s safeguards to uncover its highly confidential system prompt—the underlying instructions shaping…
A relatively unknown ransomware group named Bashe, potentially linked to the infamous LockBit gang, has launched a cyberattack on ICICI…
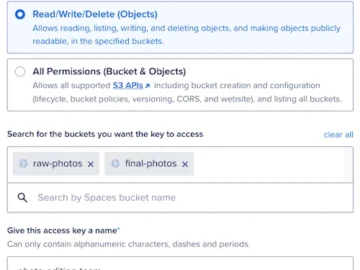
DigitalOcean announced Per-Bucket Access Keys for DigitalOcean Spaces, its S3-compatible object storage service. This feature provides customers with identity-based, bucket-level…
Jan 23, 2025Ravie LakshmananMalware / Threat Intelligence Cybersecurity researchers have disclosed details of a new BackConnect (BC) malware that has…
The ClamAV team has announced the release of security patch updates for ClamAV versions 1.4.2 and 1.0.8. These updates address…
A critical zero-day vulnerability (CVE-2025-23006) affecting SonicWall Secure Mobile Access (SMA) 1000 Series appliances is being exploited by attackers. “We…
A newly discovered attack technique, dubbed the “cookie sandwich,” enables attackers to bypass the HttpOnly flag on certain servers, exposing…
ClamAV, a widely used open-source antivirus software, has released security patch updates to address a critical buffer overflow vulnerability (CVE-2025-20128)….
Cisco addresses a critical privilege escalation bug in Meeting Management Pierluigi Paganini January 23, 2025 Cisco addressed a critical flaw…
A sophisticated supply chain attack targeting Chrome browser extensions has compromised at least 35 Chrome extensions, potentially exposing over 2.6…