A newly discovered attack technique, dubbed the “cookie sandwich,” enables attackers to bypass the HttpOnly flag on certain servers, exposing…
ClamAV, a widely used open-source antivirus software, has released security patch updates to address a critical buffer overflow vulnerability (CVE-2025-20128)….
Cisco addresses a critical privilege escalation bug in Meeting Management Pierluigi Paganini January 23, 2025 Cisco addressed a critical flaw…
A sophisticated supply chain attack targeting Chrome browser extensions has compromised at least 35 Chrome extensions, potentially exposing over 2.6…
A newly exposed vulnerability in Ruby on Rails applications allows attackers to achieve Remote Code Execution (RCE) through a flaw…
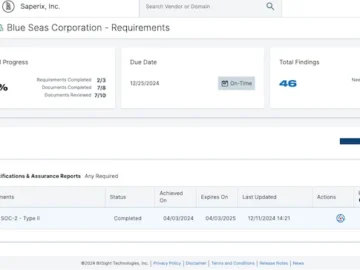
Bitsight unveiled Instant Insights, a new offering from the Bitsight IQ suite of AI-based capabilities. The new feature leverages generative…
A sophisticated supply chain attack targeting Chrome browser extensions has come to light, potentially compromising hundreds of thousands of users….
Jan 23, 2025Ravie LakshmananNetwork Security / Vulnerability Cisco has released software updates to address a critical security flaw impacting Meeting…
Netflix has dropped the first official trailer for its upcoming limited series “Zero Day”, and it’s a chilling glimpse into…
Augmented vs. Natural Having used hundreds (and built dozens) of AI applications since late 2022, I’ve come to realize something…
A new attack technique known as the “cookie sandwich” has surfaced, raising significant concerns among cybersecurity professionals. This technique enables…
U.S. President Donald Trump granted a “full and unconditional pardon” to Ross Ulbricht, Silk Road creator Pierluigi Paganini January 23,…