Ever since the MailChimp security breach on January 11, which led to the unidentified threat actors accessing one of its…
Home Affairs has set up a dedicated taskforce within its ICT division to assess its cyber security maturity against the…
Microsoft, in association with Fortinet and other partners, is working on mapping cyber crime activities and attain responses to cyber…
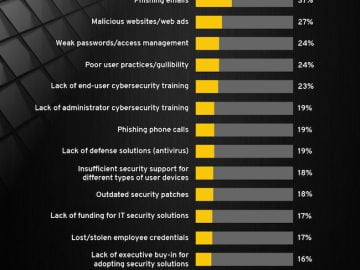
SMBs are aware of increasing cyber threats and allocating resources and investing in areas such as network and cloud security,…
Bossware helped an employer fire an accountant for not working during work time. The accountant sued for wrongful termination. The…
Hacktivist outfit Genesis Day has claimed to attack South Korean technology giant Samsung and has allegedly accessed its internal systems. …
NAB will soon begin testing its own stablecoin, AUDN, about a year after it first unveiled plans for the currency….
Hackers are setting up fake websites for popular free and open-source software to promote malicious downloads through advertisements in Google…
In earlier years, everyone depends on SOC (including firewalls, WAF, SIEM,etc.) and the priority in building the SOC provides security…
CloudSEK has developed a new app called BeVigil that can help search malicious apps downloaded on a mobile phone and…
Businesses widely use cloud applications, a fact not lost on attackers, which view these apps as an ideal home for…
We take a look at the latest fine hitting a social media network, this time over the issue of cookie…