Sophos Managed Detection and Response (MDR) has uncovered two distinct ransomware campaigns exploiting Microsoft Teams to gain unauthorized access to…
A newly identified extension for Visual Studio Code (VS Code) has been found to impersonate a legitimate Zoom application, enabling…
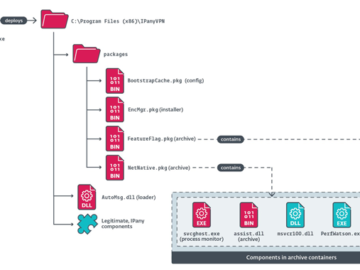
A previously undocumented China-aligned advanced persistent threat (APT) group named PlushDaemon has been linked to a supply chain attack targeting…
Oracle has released its January 2025 Critical Patch Update (CPU), addressing 318 newly discovered security vulnerabilities across its extensive product…
In a recent discovery, a security researcher uncovered a critical SQL injection vulnerability on Microsoft’s DevBlogs website (accessible at https://devblogs.microsoft.com). This…
A 7-Zip bug allows to bypass the Mark of the Web (MotW) feature Pierluigi Paganini January 22, 2025 A vulnerability…
The foundation of a successful partnership is a shared commitment to mutual growth – this is something we firmly believe…
A recent investigation has revealed that attackers are exploiting vulnerabilities in IBM i Access Client Solutions (ACS) to steal Windows…
The Mirai botnet unleashed a record-breaking Distributed Denial of Service (DDoS) attack on October 29, 2024, peaking at an astonishing…
T-Mobile, one of the leading telecom providers in the United States, has announced a significant update regarding its efforts to…
PowerSchool, a leading provider of cloud-based software used by schools to manage student information, experienced a cybersecurity incident. The PowerSchool…
0-Click Deanonymization Attack Exploits Telegram, Signal, Discord, & Other AppsA new zero-click deanonymization attack has been discovered that can potentially…