AI SPERA, a leading Cyber Threat Intelligence (CTI) provider, has collaborated with OnTheHub, a global provider of software in education,…
Torrance, United States / California, January 22nd, 2025, CyberNewsWire AI SPERA, a leading Cyber Threat Intelligence (CTI) provider, has collaborated…
Jan 22, 2025Ravie LakshmananVulnerability / Enterprise Security Oracle is urging customers to apply its January 2025 Critical Patch Update (CPU)…
David Pekoske, the Administrator of the Transportation Security Administration (TSA), was removed from his position by the Trump administration. Pekoske,…
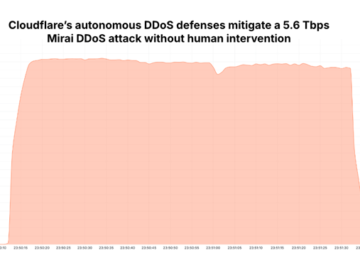
Cloudflare recently thwarted the largest distributed denial-of-service (DDoS) attack ever recorded, peaking at an unprecedented 5.6 terabits per second (Tbps)….
The Cybersecurity and Infrastructure Security Agency (CISA) announced three new Industrial Control Systems (ICS) advisories. These advisories provide critical insights…
Torrance, United States / California, January 22nd, 2025, CyberNewsWire AI SPERA, a leading Cyber Threat Intelligence (CTI) provider, has collaborated…
In today’s increasingly connected world, industrial control systems (ICS) play a pivotal role in managing and operating critical infrastructure. From…
Jan 22, 2025Ravie LakshmananBotnet / Network Security Web infrastructure and security company Cloudflare on Tuesday said it detected and blocked…
Microsoft and OpenAI have announced an extension and evolution of their strategic partnership, reinforcing their commitment to advancing artificial intelligence…
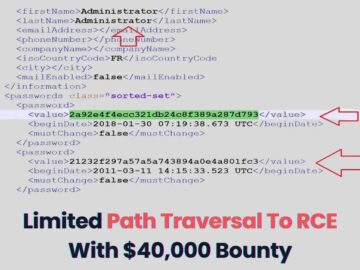
Cybersecurity researchers Abdullah Nawaf and Orwa Atyat, successfully escalated a limited path traversal vulnerability into a full-blown remote code execution…
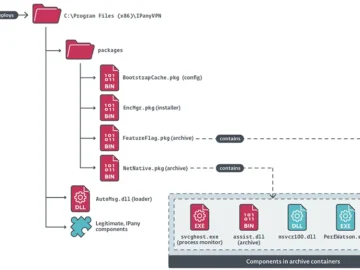
ESET researchers have uncovered a supply chain attack targeting a South Korean VPN provider, carried out by PlushDaemon, a newly…