By now, you will almost certainly be aware of the transformative impact artificial intelligence (AI) technologies are having on the…
A new cyberattack targeting German entities has recently been uncovered by Cyble Research and Intelligence Labs (CRIL). This attack leverages…
Asylum seekers residing in a Greek refugee camp funded by the European Union (EU) are subjected to invasive phone confiscations…
A recent ransomware attack has caused Blacon High School, located on the outskirts of Chester, to close temporarily. Initially, the…
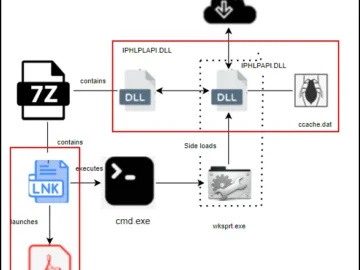
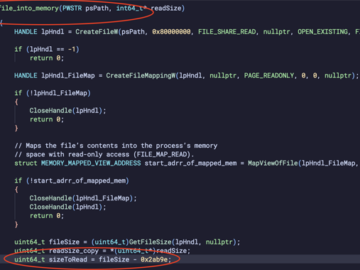
Jan 21, 2025Ravie LakshmananCyber Attack / Windows Security Cybersecurity researchers are calling attention to a series of cyber attacks that…
In today’s digital landscape, cyber threats are becoming more sophisticated and frequent, requiring organizations to adopt advanced security measures to…
CISO Sempra Infrastructure | USA | Hybrid – View job details As a CISO, you will develop and implement a…
Coles has elevated its head of digital strategy, analytics and transformation Ben Levinson to the role of general manager for…
We’ve entered a new era where verification must come before trust, and for good reason. Cyber threats are evolving rapidly,…
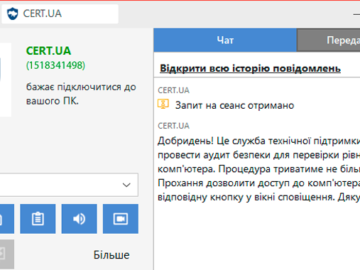
Jan 21, 2025Ravie LakshmananMalware / Cyber Threat The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts…
In this Help Net Security, Nicholas Jackson, Director of Cyber Operations at Bitdefender, discusses how technologies like AI, quantum computing,…
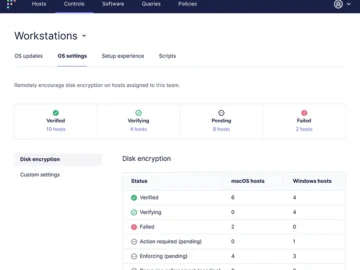
Fleet is an open-source platform for IT and security teams managing thousands of computers. It’s designed to work seamlessly with…