The UK government has announced wide-ranging plans to overhaul the way technology is funded, implemented and acquired across the public…
HPE is investigating IntelBroker’s claims of the company hack Pierluigi Paganini January 20, 2025 HPE is probing claims by the…
Esperts found new DoNot Team APT group’s Android malware Pierluigi Paganini January 20, 2025 Researchers linked the threat actor DoNot…
Microsoft has reminded admins that Exchange 2016 and Exchange 2019 will reach the end of extended support in October and…
Meta’s Facebook, Elon Musk’s X, Google’s YouTube and other tech companies have agreed to do more to tackle online hate…
Hewlett Packard Enterprise (HPE) is investigating claims of a new breach after a threat actor said they stole documents from…
President Donald Trump is expected to grant TikTok more time to strike a deal after he returns to power as…
FortiGate firewall leak exposes 15,000+ configurations, impacting organizations globally. The actor behind the leak is Belsen Group. Learn how to…
Microsoft has fixed a bug that was causing some Windows Server 2022 systems with two or more NUMA nodes to…
Jan 20, 2025Ravie LakshmananAndroid / Malware The Threat actor known as DoNot Team has been linked to a new Android…
Ever found yourself locked out of an account at the worst possibility? While rushing to meet a deadline or accessing…
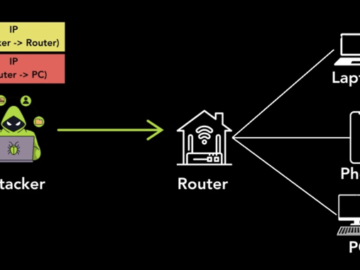
Jan 20, 2025Ravie LakshmananNetwork Security / Vulnerability New research has uncovered security vulnerabilities in multiple tunneling protocols that could allow…