The Federal Trade Commission (FTC) will require web hosting giant GoDaddy to implement basic security protections, including HTTPS APIs and mandatory…
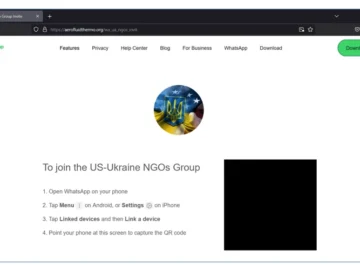
Microsoft’s Threat Intelligence teams have uncovered and exposed a spear phishing campaign targeting WhatsApp accounts, attributed to the Russian-linked hacker…
Star Blizzard, a threat actor tied to the Russian Federal Security Service (FSB), was spotted attempting to compromise targets’ WhatsApp…
Existing artificial intelligence (AI) models available in the public domain fail to provide “complexities and nuances of the past”, and…
Microsoft has started the forced rollout of Windows 11 24H2 to eligible, non-managed systems running the Home and Pro editions…
Buzz about big data permeated tech conversations in the mid-1990s, but people today don’t talk as much about big data…
Jan 17, 2025Ravie LakshmananFirmware Security / Vulnerability Cybersecurity researchers have disclosed three security flaws in Planet Technology’s WGS-804HPT industrial switches…
It is widely acknowledged that CIOs (and other tech leaders such as CTOs) on average spend a relatively short time…
Cyberattacks have become increasingly sophisticated, with more advanced technologies than ever at the disposal of cybercriminals. In 2025, cybercrime damages…
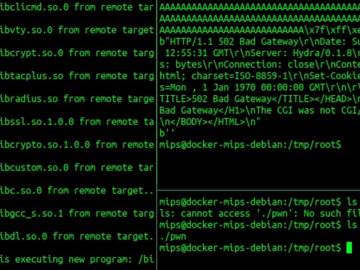
Jan 17, 2025Ravie LakshmananWeb Security / Botnet Cybersecurity researchers have exposed a new campaign that targets web servers running PHP-based…
The digital landscape is evolving rapidly, presenting security leaders with unprecedented challenges. As threats increase in volume and complexity, exacerbated…
A leading provider of hardware authentication security keys, Yubico has recently disclosed a significant vulnerability in its PAM (Pluggable Authentication…