Google Calendar, with over 500 million active users worldwide and availability in 41 languages, has long been celebrated for its…
The AhnLab Security Intelligence Center (ASEC) has detected a new strain of malware targeting poorly protected Linux SSH servers. This…
Interlock Ransomware Targets Texas Tech University Health Sciences Center A relatively unknown ransomware group, Interlock, has reportedly targeted the Texas…
Google’s Mandiant FLARE team has unveiled XRefer, a cutting-edge tool designed to streamline the complex process of malware analysis. This…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued Binding Operational Directive (BOD) 25-01: Implementing Secure Practices for Cloud Services,…
The chemical sector plays a crucial role in the global economy, providing essential materials for industries ranging from pharmaceuticals to…
Dec 18, 2024Ravie LakshmananCyber Attack / Vulnerability Threat actors are attempting to exploit a recently disclosed security flaw impacting Apache…
File upload vulnerabilities are fun to find, they are impactful by nature and in some cases even result in remote…
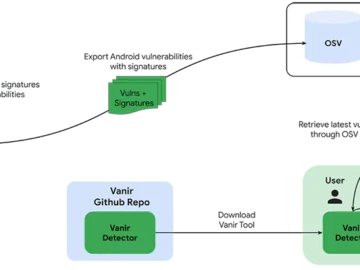
Google’s open-source tool Vanir enables Android developers to quickly scan custom platform code for missing or applicable security patches. By…
Dec 18, 2024Ravie LakshmananData Breach / Privacy Meta Platforms, the parent company of Facebook, Instagram, WhatsApp, and Threads, has been…
What was once primarily a technical role, CISOs now find themselves accountable for organizational risk, regulatory compliance, and even legal…
Cyberattacks this year have escalated into a high-stakes battle, with increasingly advanced attacks targeting critical infrastructure, personal data, and corporate…