In an era where customer expectations are higher than ever, integrating artificial intelligence (AI) into client relationships has become a…
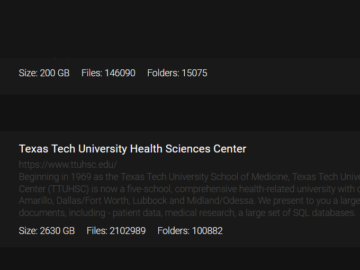
Texas Tech University data breach impacted 1.4 million individuals Pierluigi Paganini December 17, 2024 Texas Tech University reports a data…
A cyberespionage threat group known as ‘Bitter’ was observed targeting defense organizations in Turkey using a novel malware family named…
The early 2020’s saw multiple threads of the cyber threat landscape evolve. This was mostly as individual strands, rather than…
The AhnLab Security Intelligence Center (ASEC) has uncovered a new strain of DDoS malware, named cShell, targeting poorly managed Linux…
In February 2024, Serbian journalist Slaviša Milanov was taken to a police station following what seemed like a routine traffic…
The NSW government has transitioned 60,000 users to its new SAP system following a massive consolidation program costing almost $200…
CISA has issued this year’s first binding operational directive (BOD 25-01), ordering federal civilian agencies to secure their cloud environments…
A critical security vulnerability has been identified in Apache Struts, a popular open-source framework for building Java-based web applications actively…
Pet care retailer Petbarn is offering a generative AI tool to “pet parents” that can dispense “vet-approved advice” when its…
SUMMARY: Partial Data Leak: Hackers leaked 2.9GB of Cisco’s data on Breach Forums on December 16, 2024. Exposed Records: The…
The government has been asked to compile and maintain an independent map of mobile and broadband service availability and providers,…