Online harms regulator Ofcom has published its first code of practice for tackling illegal harms under the Online Safety Act…
Workers set up legitimate-looking social media accounts they can use to target potential victims, and they follow scripts for interacting…
Data breaches impacted more than 1 billion users in the first half of 2024, up 409% from this time last year, emphasizing the…
Dec 17, 2024The Hacker NewsWebinar / Risk Management Even the best companies with the most advanced tools can still get…
The government has published the latest set of public sector applications that use artificial intelligence (AI) or automation, in a…
“We were wondering if you will be interested in having a trip with our products,” one Instagram account messaged me…
A recent campaign dubbed FLUX#CONSOLE has come to light, leveraging Microsoft Common Console Document (.MSC) files to infiltrate systems with backdoor malware….
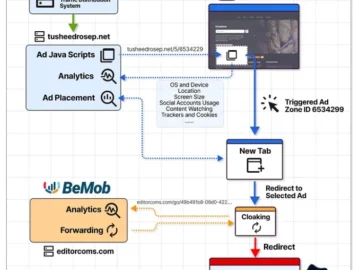
A large-scale malvertising campaign distributing the Lumma infostealer malware via intrusive “ads” leading to fake CAPTCHA pages has been tied…
It has been a year of real highs and lows for the hyperscale cloud giants, with the big three all…
A critical Remote Code Execution (RCE) vulnerability (CVE-2024-6386), affecting over 1,000,000 active installations of the WordPress Multilingual Plugin (WPML). This…
The Texas Tech University Health Sciences Center (TTUHSC) and Texas Tech University Health Sciences Center El Paso (TTUHSC El Paso),…
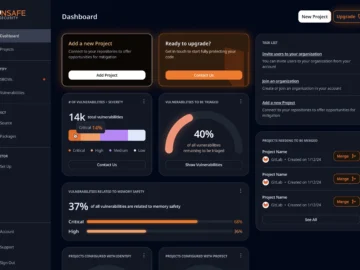
RunSafe Security has released the RunSafe Security Platform that automates risk identification, exploit prevention, and runtime software monitoring. Now, developers…