Two Belfast journalists were unlawfully placed under surveillance by two UK police forces, which spied on their phone communications and…
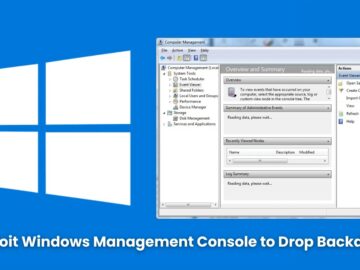
Securonix Threat Research team has uncovered a sophisticated tax-related phishing campaign that employs Microsoft Common Console Document (MSC) files and…
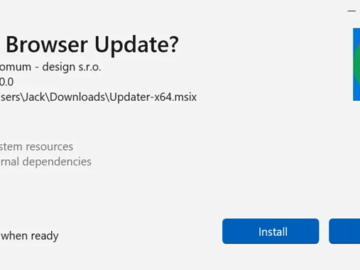
Bogus software update lures are being used by threat actors to deliver a new stealer malware called CoinLurker. “Written in…
As we approach the end of 2024, the question of whether IT sustainability remains a priority in boardrooms is more…
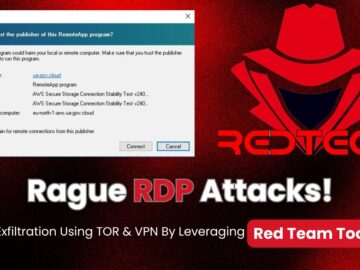
In a striking display of cyber sophistication, the advanced persistent threat (APT) group Earth Koshchei, also tracked as APT29 or…
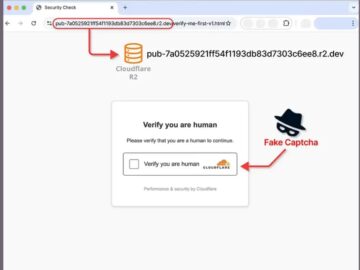
Malicious actors have taken cybercrime to new heights by exploiting captcha verification pages, a typically harmless security feature, to launch…
The government has promised financial redress and justice for subpostmasters who suffered as a result of unexplained losses when using…
U.S. CISA adds Microsoft Windows Kernel-Mode Driver and Adobe ColdFusion flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini December…
Kali Linux 2024.4 includes a broad set of updates and changes. The summary of the changelog since the 2024.3 release…
Thank you for joining! Access your Pro+ Content below. 17 December 2024 Technology on the beat Share this item with…
Researchers have identified a critical set of HTTP Response Splitting vulnerabilities in Kerio Control, a widely used Unified Threat Management…
Kali Linux has unveiled its final release for 2024, version Kali Linux 2024.4, packed with notable updates, including new tools…