File upload vulnerabilities are fun to find, they are impactful by nature and in some cases even result in remote…
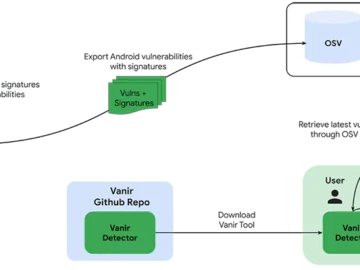
Google’s open-source tool Vanir enables Android developers to quickly scan custom platform code for missing or applicable security patches. By…
Dec 18, 2024Ravie LakshmananData Breach / Privacy Meta Platforms, the parent company of Facebook, Instagram, WhatsApp, and Threads, has been…
What was once primarily a technical role, CISOs now find themselves accountable for organizational risk, regulatory compliance, and even legal…
Cyberattacks this year have escalated into a high-stakes battle, with increasingly advanced attacks targeting critical infrastructure, personal data, and corporate…
In this Help Net Security interview, Vivek Agarwal, Privacy Program Manager at Meta Platforms, shares insights on strategies for reducing…
“We are not doing AI for the sake of it. We’re doing it with purpose.” — James Rail, QUT Hear…
Breaches in 2024 had less impact on consumers’ trust in brands compared to the previous year (a 6.5% decrease from…
The Cybersecurity and Infrastructure Security Agency (CISA) has released Binding Operational Directive (BOD) 25-01, mandating federal civilian agencies to enhance…
New technologies like generative AI and automation offer promising new ways of improving operational efficiency, but if you’re working to…
“Employees need to understand the role that AI is playing in their working life and in the relationships they have…
The Australian Energy Market Operator (AEMO) is to receive $728.1 million to upgrade its core digital systems over the next…