There is no denying the impact artificial intelligence (AI) – in particular, generative AI (GenAI) – is having on business…
An unfamiliar type of scam has surged against everyday people, with a year-over-year increase of some 400%, putting job seekers…
The Horizon system was the vehicle used by humans at the Post Office to carry out sustained abuse of subpostmasters…
Healthcare software as a service (SaaS) company Phreesia is notifying over 910,000 people that their personal and health data was…
In a significant move that will reshape the cybersecurity landscape, Arctic Wolf and BlackBerry Limited (NYSE: BB; TSX:BB) announced today…
Bulletproof hosting services, a type of dark internet service provider, offer infrastructure to cybercriminals, facilitating malicious activities like malware distribution,…
This week on the Lock and Code podcast… Privacy is many things for many people. For the teenager suffering from…
Rhode Island State House (Image: MOHANN) Rhode Island is warning that its RIBridges system, managed by Deloitte, suffered a data breach…
Researchers have discovered a new Android banking trojan targeting Indian users, and this malware disguises itself as essential utility services…
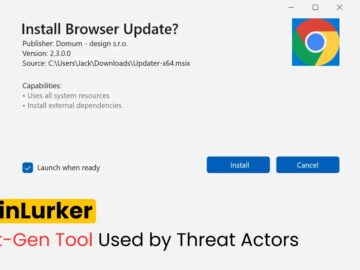
CoinLurker is a sophisticated data-stealing malware that has revolutionized fake update campaigns. Written in the Go programming language, CoinLurker incorporates…
Researchers discovered multiple vulnerabilities in Ruijie Networks’ cloud-connected devices. By exploiting these vulnerabilities, attackers can remotely compromise access points, gain…
SUMMARY Arrest and Charges: Baron Martin, 20, arrested for producing child sexual abuse material and cyberstalking, linked to extremist networks…