Cybersecurity researchers have discovered a new PHP-based backdoor called Glutton that has been put to use in cyber attacks targeting…
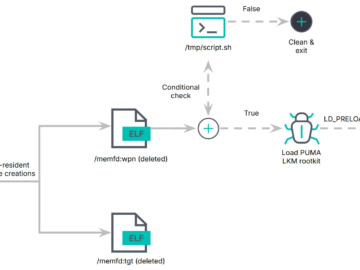
PUMAKIT, a sophisticated rootkit that uses advanced stealth mechanisms Pierluigi Paganini December 15, 2024 Researchers discovered PUMAKIT, a Linux rootkit…
A new wave of cyberattacks has emerged, targeting YouTube creators through malicious collaboration requests that exploit the trust between creators…
Dec 16, 2024Ravie LakshmananCryptocurrency / Phishing Attack Cybersecurity researchers are calling attention to a new kind of investment scam that…
We have witnessed an undeniable backlash against sustainability this year. Despite the news cycle being awash with coverage of the…
Telecom Namibia has fallen victim to a cyberattack, resulting in the leak of over 400,000 customer files. The Telecom Namibia…
Multiple flaws in Volkswagen Group’s infotainment unit allow for vehicle compromise Pierluigi Paganini December 16, 2024 Researchers discovered multiple flaws…
Multiple flaws in Volkswagen Group’s infotainment unit allow for vehicle compromise Pierluigi Paganini December 16, 2024 Researchers discovered multiple flaws…
Rhode Island is tackling with a major cybersecurity breach that has compromised the personal information of thousands of residents. The…
A critical Remote Code Execution (RCE) vulnerability has been discovered in a popular open-source biomedical tool used worldwide. This vulnerability,…
December 13, 2024 – Care1, a Canadian healthcare solutions provider left a cloud storage instance freely accessible and unencrypted for…
The latest Sensor Intelligence Report from Cyble, dated December 4–10, 2024, sheds light on a troubling increase in cyber threats,…