Serbian police and intelligence services have been reported to use advanced phone spyware in conjunction with mobile forensic tools to…
Man-in-the-middle (MITM) attacks are a significant cybersecurity threat, where an attacker intercepts and potentially alters communication between two parties without…
The Cybersecurity and Infrastructure Security Agency (CISA) and the Environmental Protection Agency (EPA) have jointly released a crucial fact sheet…
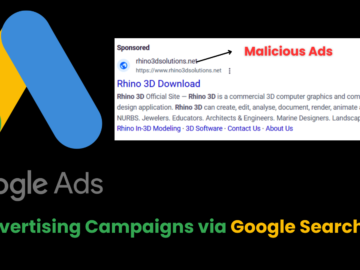
Threat researchers have identified a persistent series of malvertising campaigns targeting graphic design professionals, using Google Search ads as a…
The clock is ticking for financial institutions across the EU as the January 17, 2025, deadline for the Digital Operational…
In this Help Net Security interview, Emre Kazim, Co-CEO of Holistic AI, discusses the need for companies to integrate responsible…
Trapster Community is an open-source, lightweight, low-interaction honeypot designed for deployment within internal networks. It enhances network security by creating…
On December 15, we detected a malicious campaign targeting Kaiser Permanente employees via Google Search Ads. The fraudulent ad masquerades…
Platform security – securing the hardware and firmware of PCs, laptops and printers – is often overlooked, weakening cybersecurity posture…
Security researchers have uncovered several high-severity vulnerabilities in the popular Mullvad VPN service that could allow attackers to execute malicious…
Lotterywest is recruiting for new security leadership to oversee its “highly integrated” cyber systems and practices. The Western Australia’s lotteries…
Queensland’s chief customer and digital officer of nearly three years Chris McLaren will step down at the end of this…