A sophisticated attack campaign targeting organizations in Japan and other East Asian countries. The threat actor, identified as APT-C-60, is…
Over 336,000 Prometheus servers and Exporters were exposed to DoS attacks, allowing attackers to obtain sensitive information such as credentials…
American neo-Nazi Robert Rundo’s six-year “battle with the feds”—a fight that spans two dismissals, three appellate reversals, and an extradition…
As we step into 2025, the cybersecurity landscape is at a pivotal juncture. The challenges of AI-driven threats, evolving data…
Security researchers at Elastic Security Labs have uncovered a sophisticated Linux malware dubbed PUMAKIT, which employs advanced stealth techniques and…
This year’s Black Hat Europe showcased the latest advancements in research, developments and emerging trends in cybersecurity. Being surrounded by…
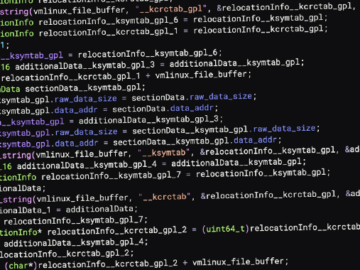
Dec 13, 2024Ravie LakshmananLinux / Threat Analysis Cybersecurity researchers have uncovered a new Linux rootkit called PUMAKIT that comes with…
Dell has recently disclosed two critical security vulnerabilities affecting a wide range of its products, potentially exposing numerous systems to…
The cyberthreat landscape has shifted rapidly over the past several years, and this evolution will continue in 2025. AI has…
Regression testing is a crucial part of software development that ensures new code changes don’t negatively affect existing functionality. It…
The holiday season is a time for celebration, with organisations hosting festive parties and employees spending time with family. However,…
Experts discovered the first mobile malware families linked to Russia’s Gamaredon Pierluigi Paganini December 13, 2024 The Russia-linked APT Gamaredon…