Microsoft has released the Windows 11 KB5050009 and KB5050021 cumulative updates for versions 24H2 and 23H2 to fix security vulnerabilities…
Cybersecurity is facing new challenges with advances in AI, cloud tech, and increasing cyber threats. Solutions like blockchain are emerging…
Jan 14, 2025Ravie LakshmananVulnerability / Data Privacy New research has pulled back the curtain on a “deficiency” in Google’s “Sign…
A weakness in Google’s OAuth “Sign in with Google” feature could enable attackers that register domains of defunct startups to…
Fortinet has released a security update with the fixes for 15 vulnerabilities that affect multiple products with distinct security issues,…
Fortinet has patched an authentication bypass vulnerability (CVE-2024-55591) affecting its FortiOS firewalls and FortiProxy web gateways that’s being exploited by…
Jan 14, 2025Ravie LakshmananEndpoint Security / Vulnerability Microsoft has shed light on a now-patched security flaw impacting Apple macOS that,…
A law firm based in Manchester has gathered around 15,000 claimants for an impending data breach lawsuit against Microsoft and…
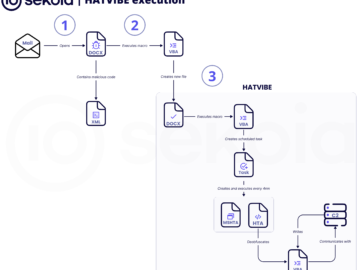
Russia-linked APT UAC-0063 target Kazakhstan in with HATVIBE malware Pierluigi Paganini January 14, 2025 Russia-linked threat actor UAC-0063 targets Kazakhstan…
The ideal number of human employees in any company is zero. This is a flaw of capitalism, not automation, yet…
Attackers are exploiting a new authentication bypass zero-day vulnerability in FortiOS and FortiProxy to hijack Fortinet firewalls and breach enterprise…
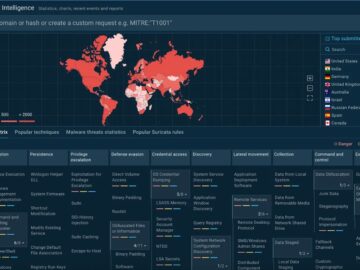
Effective cyber threat detection and response depend on the ability to access actionable, real-time intelligence. ANY.RUN, a trusted name in…