Prepare for the 2025 altcoin season: experts predict rising interest in altcoins like WorldCoin, driven by Web3, blockchain, and metaverse…
What do identity risks, data security risks and third-party risks all have in common? They are all made much worse…
Thank you for joining! Access your Pro+ Content below. 14 January 2025 Generating customer experience at NatWest Bank Share this…
Threat actors exploit Aviatrix Controller flaw to deploy backdoors and cryptocurrency miners Pierluigi Paganini January 14, 2025 A critical vulnerability…
Cybersecurity researchers at EXPMON have uncovered an intriguing “zero-day behavior” in PDF samples that could potentially be exploited by attackers…
A widespread campaign targeting Fortinet FortiGate firewall devices with exposed management interfaces on the public internet. The attacks, observed by…
Jan 14, 2025Ravie LakshmananVulnerability / Network Security Threat hunters are calling attention to a new campaign that has targeted Fortinet…
Debate is raging about whether the UK government’s push to grow the number of homegrown datacentres with capabilities to host…
A critical vulnerability in Google’s “Sign in with Google” authentication flow is putting millions of Americans at risk of data…
A critical flaw in Google’s “Sign in with Google” authentication system has left millions of Americans vulnerable to potential data…
Jan 14, 2025Ravie LakshmananCryptocurrency / Online Scam The Telegram-based online marketplace known as HuiOne Guarantee and its vendors have cumulatively…
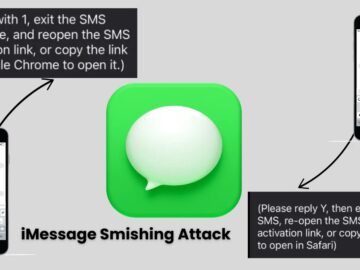
A new smishing (SMS phishing) campaign is making waves, specifically targeting iMessage users by manipulating Apple’s built-in phishing protections. Users…