U.S. CISA adds BeyondTrust PRA and RS and Qlik Sense flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini January…
Blood-donation not-for-profit OneBlood confirms that donors’ personal information was stolen in a ransomware attack last summer. OneBlood first notified the public…
Nvidia faces a significant revenue threat due to the latest US export restrictions on artificial intelligence chips, designed to limit…
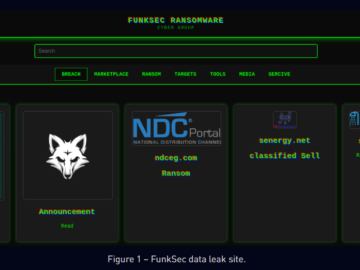
Inexperienced actors developed the FunkSec ransomware using AI tools Pierluigi Paganini January 13, 2025 FunkSec, a new ransomware group that…
It’s not easy for firms to understand how to comply with global security and resilience regulation; there’s no single place…
NBN Co will receive up to $3 billion from the federal government and chip in $800 million itself to provide…
Path of Exile 2 developers confirmed that a hacked admin account allowed a threat actor to change the password and…
CISA has tagged a command injection vulnerability (CVE-2024-12686) in BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) as actively…
The Cybersecurity and Infrastructure Security Agency (CISA) has updated its Known Exploited Vulnerabilities (KEV) Catalog with two new critical vulnerabilities,…
Optus has quietly paused the launch of its satellite-to-mobile service launch following its partnership with SpaceX’s Starlink. The Singtel-owned telco…
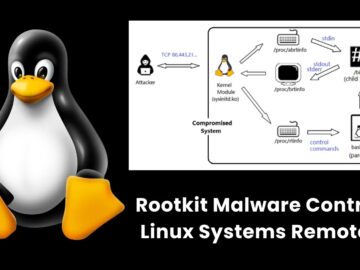
Fortinet researchers uncovered an advanced rootkit malware exploiting multiple zero-day vulnerabilities in enterprise appliances by executing a shell script (Install.sh)….
Microsoft Threat Intelligence has uncovered a critical macOS vulnerability that allowed attackers to bypass Apple’s System Integrity Protection (SIP). Known…