British Prime Minister Keir Starmer wants the UK to become the world leader for artificial intelligence, and is promising to…
Researchers analyzed new versions of the Banshee macOS Stealer sample that initially evaded detection by most antivirus engines, as analysis…
The government’s technical authority on cyber security has a new head, with Stephanie Crowe taking over as head of the…
The City of Melbourne is searching for a chief technology and information officer (CTIO) following a “recent transformation” of its…
IT decision makers are under mounting pressure to deliver solutions that are not only innovative but also resilient and adaptive….
With the advent of virtual reality, everyone got scared that the life we know will disappear, and only those who…
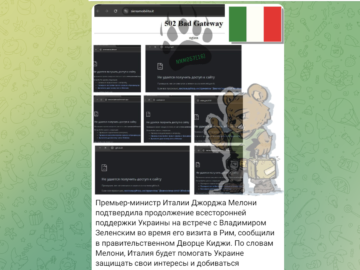
Pro-Russia hackers NoName057 targets Italy again after Zelensky’s visit to the country Pierluigi Paganini January 12, 2025 Over the weekend,…
Hewlett Packard Enterprise has struck a deal worth over US$1 billion (A$1.6 billion) to provide Elon Musk’s social media platform…
Cybercriminals are exploiting a trick to turn off Apple iMessage’s built-in phishing protection for a text and trick users into…
The Department of Justice Queensland is hiring a new chief information officer as it explores new technology opportunities. The department…
Security Affairs newsletter Round 506 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini January 12, 2025 A new round of…
What’s Old is New: Network and Web Application Vulnerabilities The first newsworthy AI breach of 2024 didn’t come from a…