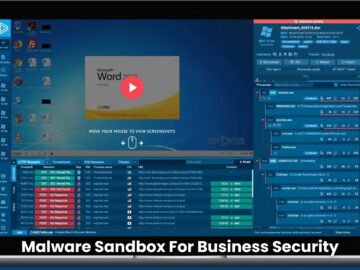
The NonEuclid Remote Access Trojan (RAT), a highly sophisticated malware, has been detected, allowing unauthorized remote access via advanced evasion…
Discover how AI revolutionizes cybersecurity with real-time threat detection, adaptive protection, and advanced data protection to combat evolving cybersecurity risks….
Jan 09, 2025Ravie LakshmananVulnerability / Endpoint Security Palo Alto Networks has released software patches to address several security flaws in…
Privacy firm Proton suffered a massive worldwide outage today, taking down most services, with Proton Mail and Calendar users still…
Imagine an employee receiving an email that looks completely legitimate, maybe it’s a fake invoice or a shipping update. They…
Then, between Christmas Eve and New Year’s, came a new deluge of swattings. They hit close to a hundred politicians…
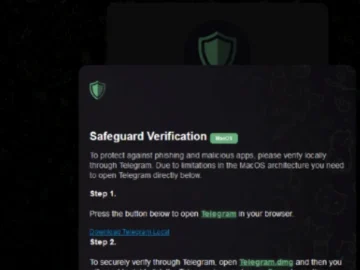
The Banshee Stealer is a stealthy threat to the rising number of macOS users around the world, including those in…
The National Police Agency (NPA) and the Cabinet Cyber Security Center in Japan have linked a cyber-espionage campaign targeting the…
As you probably know by now, it doesn’t really matter how big in size your business is, you’re going to…
Small businesses and boutique organizations should use caution when leaning on browser-friendly artificial intelligence (AI) tools to generate ideas, content,…
Hackers exploiting the critical Ivanti Connect Secure zero-day vulnerability disclosed yesterday installed on compromised VPN appliances new malware called ‘Dryhook’ and…
Criminal IP, a globally recognized Cyber Threat Intelligence (CTI) solution by AI SPERA, has launched its Criminal IP Malicious Link Detector add-in…