In the future, it might be a new mobile game or an algorithm helping students study at home. It could…
The server was exposed to the public without any password or security authentication, allowing access to tens of thousands of…
[ This article was originally published here ] By John E. Dunn Two arrests for alleged ransomware crimes and some…
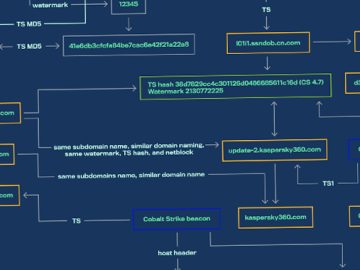
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware…
The volume of Business Email Compromise (BEC) attacks doubled during the course of 2022 thanks to several high-profile and successful…
Kali Purple 2023.1 Review Source link
Microsoft has announced a new assistant powered by artificial intelligence to help boost productivity across Microsoft 365 apps, currently being…
CISA has updated its list of security flaws that have been actively exploited, including a critical vulnerability affecting Adobe ColdFusion…
Whenever we see a YouTube video that is informative, we tend to go through the description or ‘show more’ feature…
UK chancellor Jeremy Hunt has announced new funding avenues for research and development (R&D) intensive businesses as part of the Spring…
How to setup system-wide Mullvad DNS over HTTPS on iOS and macOS Source link
ESET Research discovered the first incidence of clippers present in messaging apps. Several fake Telegram and WhatsApp websites have been…