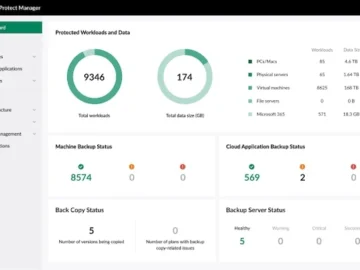
Synology releases ActiveProtect, a new line of data protection appliances designed to provide enterprises a unified backup solution with simplicity,…
For years, cyber risk was relegated to the world of information technology (IT), managed by security and engineering teams as…
As part of our Detectify under the hood blog series, we recently introduced our new engine framework and how it…
A proof-of-concept (PoC) exploit for the critical Apache Struts vulnerability, CVE-2024-53677, has been publicly released, raising alarm across the cybersecurity…
Wireshark, the popular network protocol analyzer, has reached version 4.4.3. Wireshark offers deep inspection across hundreds of protocols, live and…
A proof-of-concept (PoC) exploit code for a critical vulnerability in macOS, identified as CVE-2024-54527 has been disclosed. This vulnerability allows…
GitLab has announced the release of critical updates to its Community Edition (CE) and Enterprise Edition (EE), specifically versions 17.7.1,…
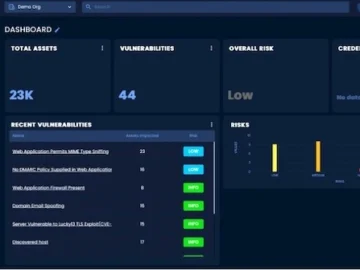
Eliminating the inefficiencies, silos, unnecessary complexity, and coverage gaps that security practitioners have faced with fragmented security tools, the newly…
Jan 09, 2025Ravie LakshmananData Privacy / GDPR The European General Court on Wednesday fined the European Commission, the primary executive…
For decades, the CIS Critical Security Controls (CIS Controls) have simplified enterprises’ efforts to strengthen their cybersecurity posture by prescribing…
As we step into 2025, many of us are setting resolutions to improve, grow, and achieve more. At Intigriti, we’re…
Multiple vulnerabilities in Palo Alto Networks’ Expedition migration tool have been discovered, potentially exposing sensitive firewall credentials, including usernames, cleartext…