A ransomware attack disrupted services at Pittsburgh Regional Transit Pierluigi Paganini December 26, 2024 A ransomware attack on Pittsburgh Regional…
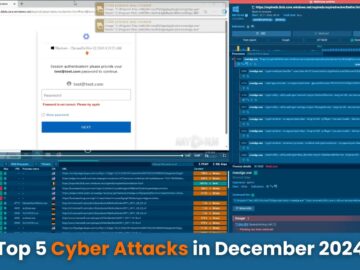
The cybersecurity research team at ANY.RUN, leveraging their Interactive Sandbox and Threat Intelligence Lookup tools, has uncovered and analyzed a…
Rail travelers across India faced disruption as the Indian Railway Catering and Tourism Corporation (IRCTC) website and mobile app went…
Japan Airlines (JAL) said its systems returned to normal, with same-day ticket sales resuming, after a cyber attack delayed some…
Cryptocurrency hacking incidents in 2024 surged 21.07% YoY to $2.2 billion, with 303 breaches reported, which marks the fifth year…
McDonald’s India (West & South) / Hardcastle Restaurants Pvt. Ltd. operates a custom McDelivery web app for ordering McDonald’s food…
Threat Analysts have reported alarming findings about the “Araneida Scanner,” a malicious tool allegedly based on a cracked version of…
A new critical vulnerability (CVE-2024-52046) has been discovered in Apache MINA, potentially allowing attackers to execute remote code by exploiting…
Every year has its own mix of digital security debacles, from the absurd to the sinister, but 2024 was particularly…
A Brazilian man, Junior Barros De Oliveira, has been charged with multiple counts of cybercrime and extortion for hacking into…
A cyber attack hit Japan Airlines delaying ticket sales for flights Pierluigi Paganini December 26, 2024 A cyberattack hit Japan…
Two malicious Python packages, Zebo-0.1.0 and Cometlogger-0.1, were recently detected by Fortinet’s AI-driven OSS malware detection system. These packages, spotted…