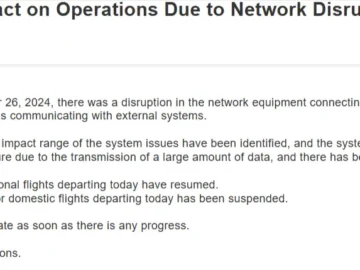
Japan Airlines (JAL) experienced an operational disruption on December 26, 2024, following a cyberattack that impacted its systems. Japan Airlines…
Adobe has issued a critical security update for ColdFusion versions 2023 and 2021 to address a major vulnerability that could…
A major dark web operation dedicated to circumventing KYC (Know Your Customer) procedures, which involves the systematic collection and exploitation…
A newly disclosed high-impact vulnerability in Dell’s widely used SupportAssist software could allow attackers to escalate privileges on affected systems….
IBM has reported vulnerabilities in its AIX operating system that could allow attackers to cause a Denial of Service (DoS)…
iProov, a leading provider of biometric identity verification solutions, has uncovered a covert dark web operation aimed at undermining Know…
Gartner created the Continuous Threat Exposure Management (CTEM) framework as a strategic approach to help organizations of all sizes and…
On Christmas Day, December 25, 2024, Japan Airlines (JAL) was struck by a significant cyber attack, disrupting both domestic and…
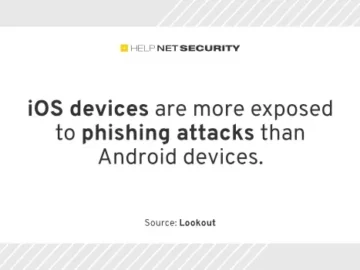
The mobile threat landscape continues to grow at an alarming rate as cybercrime groups shift their tactics and target mobile…
Service disruptions remain a critical concern for IT and business executives, with 88% of respondents saying they believe another major…
Managing cybersecurity and IT budgets is a critical element of organizational strategy. With increasing threats to data security, the rise…
Japan Airlines (JAL), the nation’s second-largest airline, reported a significant cyberattack on its systems early Thursday morning, causing disruptions to…