The Federal Trade Commission (FTC) has ordered Marriott International and Starwood Hotels to define and implement a robust customer data…
Two WordPress plugins required by the premium WordPress WPLMS theme, which has over 28,000 sales, are vulnerable to more than a dozen…
A U.S. federal judge has ruled that Israeli spyware maker NSO Group violated U.S. hacking laws by using WhatsApp zero-days…
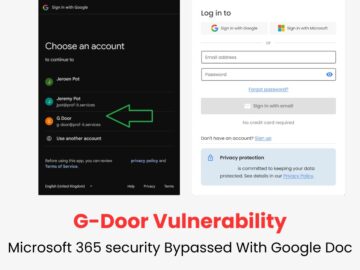
A newly discovered vulnerability, dubbed “G-Door,” allows malicious actors to circumvent Microsoft 365 security measures by exploiting unmanaged Google Docs…
Lazarus Group Targets Nuclear Power Organizations with Sophisticated Malware Campaign The Lazarus Group, a well-known hacking collective widely believed to…
U.S. Court rules against NSO Group in WhatsApp spyware Lawsuit Pierluigi Paganini December 23, 2024 A U.S. court ruled in…
Cybersecurity threats are increasingly targeting vulnerabilities in publicly exposed assets like VPNs and firewalls, exploited by various actors, including APT…
A new Microsoft 365 phishing-as-a-service platform called “FlowerStorm” is growing in popularity, filling the void left behind by the sudden shutdown of…
A joint Cybersecurity Advisory (CSA) warns of ongoing exploitation attempts by Iranian Islamic Revolutionary Guard Corps (IRGC)-affiliated cyber actors using…
Cyberattacks are as old as the internet, but over the past several years they have become more insidious and destructive,…
The US Department of Justice has unsealed charges against Rostislav Panev, 51, a dual Russian and Israeli national, suspected of…
Dec 23, 2024Ravie LakshmananMachine Learning / Threat Analysis Cybersecurity researchers have found that it’s possible to use large language models…