Signal is finally adding a new feature that allows users to synchronize their old message history from their primary iOS…
Education software giant PowerSchool has started notifying individuals in the U.S. and Canada whose personal data was exposed in a…
Broadcom, a leader in semiconductors and networking equipment, has launched its latest innovation: the Emulex Secure Fibre Channel Host Bus…
What Is Pentesting? Pentesting attempts to ethically breach a system’s security for the purpose of vulnerability identification. In most cases,…
Jan 28, 2025Ravie Lakshmanan Cybersecurity researchers have disclosed details of a now-patched account takeover vulnerability affecting a popular online travel…
Fujitsu has been forced to escalate problems with a key IT system used by Airtricity in the Republic of Ireland…
PDF generators are commonly implemented in applications. Developers tend to use these components to generate documents based on dynamic data…
As the world’s Rail transportation industry becomes more sophisticated, embracing digital technologies to enhance efficiency, safety, and operational capabilities, it…
In our hyper-connected world, cybersecurity is more critical than ever. With increasing reliance on digital technologies, individuals and organizations face a growing…
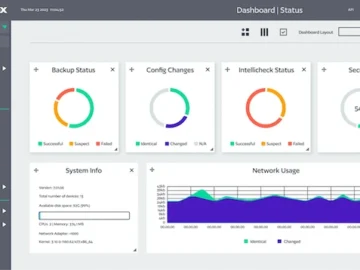
BackBox launched Network Cyber Resilience Platform. With business productivity at risk due to the complexity of managing too many tools,…
This week on the Lock and Code podcast… The era of artificial intelligence everything is here, and with it, come…
Workflow Integration Code security tools need to be accessible in the toolkit developers already use and in the workflows they…



![Bug Bounty Vs. Pentest [Differences Explained] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2025/01/Bug-Bounty-Vs-Pentest-Differences-Explained-360x270.png)