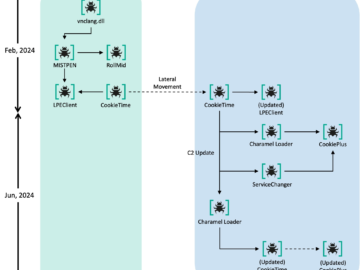
Lazarus APT targeted employees at an unnamed nuclear-related organization Pierluigi Paganini December 23, 2024 North Korea-linked Lazarus Group targeted employees…
A critical vulnerability in the popular PHP-based Craft CMS has been discovered, allowing unauthenticated attackers to execute remote code on…
North Korean hackers are estimated to have stolen a staggering $2.2 billion in 2024, up 21% from 2023. With advanced…
Dec 23, 2024Ravie LakshmananGDPR / Data Privacy Italy’s data protection authority has fined ChatGPT maker OpenAI a fine of €15…
A staggering 17 million patient records, containing sensitive personal and medical information, have been stolen in a devastating ransomware attack…
Germany has launched an investigation into reports of a significant cyber threat believed to be linked to the BadBox Malware,…
The Chinese National Internet Emergency Center has discovered and resolved two significant cases of cyber espionage targeting Chinese technology companies…
After a prolonged legal battle stretching over five years, WhatsApp has triumphed over NSO Group in a significant lawsuit concerning…
As we approach the end of 2024, it’s clear that the landscape of cyber threats has continued to evolve at…
Evilginx is an open-source man-in-the-middle attack framework designed to phish login credentials and session cookies, enabling attackers to bypass 2FA…
SHARP has issued an urgent security advisory regarding multiple vulnerabilities discovered in several of its router products. Customers using the…
In this Help Net Security interview, Jason Passwaters, CEO of Intel 471, discusses how integrating cybercrime intelligence into an organization’s…