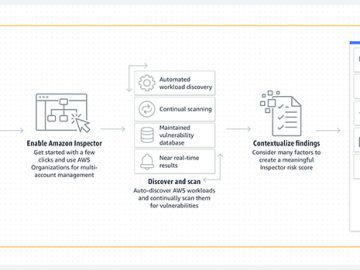
Amazon Inspector is designed to manage vulnerabilities by continuously scanning your AWS workloads for software vulnerabilities and unintended network exposure…
Federal agencies exist to protect and support the nation and its citizens. Despite their elaborate processes to reduce cyber risk,…
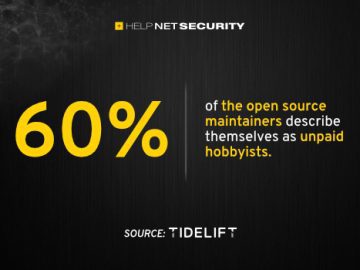
Ensuring the security of the open-source software that modern organizations depend on is a crucial responsibility of the open source…
Be sure to catch the full webinar on Wednesday, May 10, 2023. Don’t miss our upcoming webinar on EDR vs. MDR!…
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings,…
Google has promised to add end-to-end encryption to Google Authenticator backups after users were warned against turning on the new…
We take a look at Google’s efforts to shut down a particularly nasty set of modified Chrome installs playing host…
Important Links: RegistrationThe Paranoids Event OverviewThe Paranoids Event Insights Contact [email protected] for any questions! We are so excited to have you participate…
The Ukrainian Government Computer Emergency Response Team (CERT-UA) has released a new alert in which it states that Russian hackers…
An easy to exploit vulnerability in Oracle WebLogic Server has been added to the CISA list of things you really,…
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings,…
OpenAI has introduced a feature that lets you opt your conversations out of ChatGPT’s training data, but you have to…