In today’s digital age, YouTube has become a platform where individuals, especially those between the ages of 14 and 33,…
Dec 20, 2024Ravie LakshmananVulnerability / Cyber Attack A now-patched critical security flaw impacting Fortinet FortiClient EMS is being exploited by…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued eight detailed advisories on vulnerabilities affecting Industrial Control Systems (ICS). These…
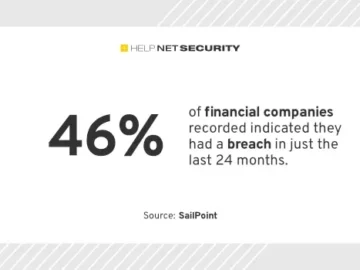
As the financial industry is the most targeted sector for data breaches in 2024, it’s now more important than ever…
A new and advanced ransomware family, dubbed NotLockBit, has emerged as a significant threat in the cybersecurity landscape, closely mimicking…
In this Help Net Security interview, Anjos Nijk, Managing Director of the European Network for Cyber security (ENCS), discusses cybersecurity…
Dec 20, 2024Ravie LakshmananCISA / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security…
AI changes how organizations look at cybersecurityGenAI is compromising security while promising efficiency This article highlights key findings from 2024…
Sophos, a leading cybersecurity firm, recently announced the resolution of three critical security vulnerabilities in its Sophos Firewall product. These…
Here’s a look at the most interesting products from the past week, featuring releases from Appdome, GitGuardian, RunSafe Security, Stairwell,…
The beloved doughnut chain Krispy Kreme has fallen victim to a significant cybersecurity incident, with the notorious Play ransomware group…
The Digital Transformation Agency will move ahead with a transparency crackdown on hospitality from ICT suppliers to government personnel, following…