As outside economic pressures continue to shape how organizations think and allocate resources, data security continues to be a high…
Not all cybersecurity budgets are made equal, and for some that means having too many or too few tools. For…
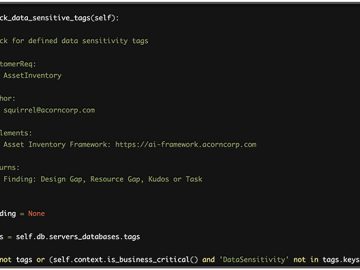
Development teams utilize automation through Infrastructure as Code (IaC) to facilitate rapid and frequent changes to their cloud-native architectures. Security…
Hopefully, you’ve been working with the Center for Internet Security (CIS) on securing your cloud infrastructure for a while now….
HackerOne Brand Ambassadors are leaders who have a passion to bring the community together in their local city or region….
By Dan Benjamin, Co-Founder and CEO, Approximately of corporate data now lives in the cloud, a number that has doubled…
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings,…
With their continued accomplishments in the racing world, Amna Qubaisi and Hamda Qubaisi are all set to drive their family’s…
Happy Conflu week, Well, I got sick (again) from RSA. The swag at these cons continues to decline. Still…
A tool that’s harvesting pictures to train image-generating AIs has caused some measure of chaos among webmasters who’d rather their…
Addressing security risks at scale is more important than ever. With a global pandemic accelerating digital transformations, organizations are shipping…
T-Mobile USA has started alerting customers whose personal information and account data may have been exposed as a consequence of…