Sonic, the leading gaming SVM on Solana, and Injective, a WASM-based L1 network, today announced that they will team up…
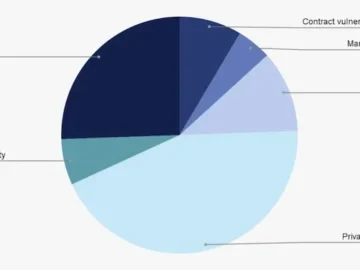
$2.2 billion worth of cryptocurrency was stolen from various platforms in 2024, Chainalysis’ 2025 Crypto Crime Report has revealed. Of…
Dec 19, 2024Ravie LakshmananSupply Chain / Software Security Threat actors have been observed uploading malicious typosquats of legitimate npm packages…
Cybersecurity researchers have uncovered active exploitation of a critical vulnerability in Fortinet’s FortiClient Enterprise Management Server (EMS), tracked as CVE-2023-48788….
Europol has published a groundbreaking report titled “Leveraging Legitimacy: How the EU’s Most Threatening Criminal Networks Abuse Legal Business Structures.” The…
As 2024 comes to a close and we reach the midpoint of a decade that might generously be described as…
Fortinet warns about Critical flaw in Wireless LAN Manager FortiWLM Pierluigi Paganini December 19, 2024 Fortinet warns of a patched…
A critical security configuration in Azure Key Vault has been discovered, potentially allowing users with the Key Vault Contributor role…
BADBOX is a cybercriminal operation infecting Android devices like TV boxes and smartphones with malware before sale, which are often…
KEY SUMMARY POINTS Google Calendar Targeted: Hackers are exploiting Google Calendar’s features to send phishing emails disguised as legitimate invites….
Joseph Cox, author of the 2024 book “Dark Wire: The Incredible True Story of the Largest Sting Operation Ever“, came…
Dec 19, 2024Ravie LakshmananMalware / Botnet Juniper Networks is warning that Session Smart Router (SSR) products with default passwords are…