Dec 19, 2024Ravie LakshmananVulnerability / Network Security Fortinet has issued an advisory for a now-patched critical security flaw impacting Wireless…
Five judges will hear a case against 30 people accused of being involved in the distribution of encrypted mobile phones…
In recent years, cyber attackers have continuously upgraded their tactics, exploiting a variety of tools and techniques to evade detection…
A sophisticated phishing campaign targeting European companies. The attack, which peaked in June 2024, aims to harvest Microsoft Azure cloud…
A high-severity vulnerability has been discovered in the popular web framework, Next.js, which allows attackers to bypass authentication under specific…
Once a cornerstone of the digital promise, trust has been undermined by corporate misuse, data breaches, disinformation, and the growing…
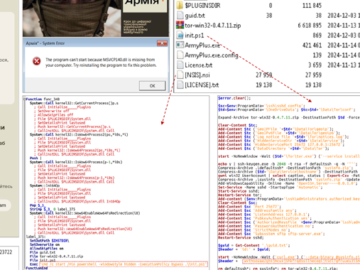
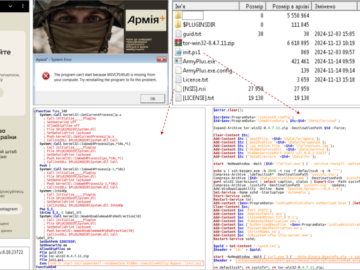
Dec 19, 2024Ravie LakshmananDisinformation / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed that a threat actor…
Artificial intelligence (AI) has hit the headlines and the datacentres, but with it comes a range of performance and operating…
CERT-UA: Russia-linked UAC-0125 abuses Cloudflare Workers to target Ukrainian army Pierluigi Paganini December 19, 2024 The Computer Emergency Response Team…
At the core of every thriving bug bounty platform lies its triage team. These teams evaluate vulnerability reports, deciding on…
A critical security vulnerability tracked as CVE-2024-51479 has been identified in Next.js, a widely used React framework for building web…
In other posts during the last year, according to the Kela analysis, cybercrime forum users have recommended Big Mama or…