There are times where an attacker can hack a system and yet nothing is sent back, and this is classified…
Reducing risk is the fundamental reason organizations invest in cybersecurity. The threat landscape grows and evolves, creating the need for…
This is a guest blog post from Detectify Crowdsource hacker, Gwendal Le Coguic. This is a tutorial on how to…
Secure data destruction and network router disposal go hand in hand when it comes to office network security. However, a…
Five years after the Defense Digital Service (DDS) launched the first-ever U.S. federal government bug bounty Challenge, we’re pleased to…
Swedish west coast native Emelie Andersson moved to the other side of the country 6 years ago to pursue a…
In April of 2021, the Defense Industrial Base Vulnerability Disclosure Program (DIB-VDP) pilot kicked off a twelve-month program to invite…
Good security starts with knowing your web assets. To enable transparency over your tech stack, we have released Asset Inventory,…
Tech giants Apple, Microsoft, and Google each fixed major security flaws in April, many of which were already being used…
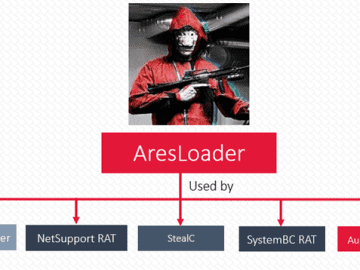
A new loader that is used to run and install additional malware on targeted systems was found by researchers at…
HackerOne recently hosted AWS and a panel of expert ethical hackers to discuss how Server-Side Request Forgery (SSRF) vulnerabilities and cloud misconfiguration are ripe…
Pulse Secure and Fortinet have announced advisories detailing a critical vulnerability found that enables an unauthenticated user to conduct file…