In a dramatic escalation of its antitrust lawsuit against Google, the U.S. Department of Justice (DOJ) has proposed sweeping changes…
As cyber attackers refine their skills, their methods evolve to exploit vulnerabilities in innovative and increasingly difficult-to-detect ways. The modern…
Critical infrastructure, the lifeblood of modern society, is under increasing threat as a new report from Censys reveals that over…
The U.S. Department of Justice has announced the seizure of the PopeyeTools website, a notorious cybercrime website that facilitated the…
A recent breach of U.S. telecommunications companies has been described recently as the “worst telecom hack in our nation’s history…
NVIDIA has issued a security advisory addressing a critical vulnerability (CVE-2024-0138) discovered in its Base Command Manager software. This flaw,…
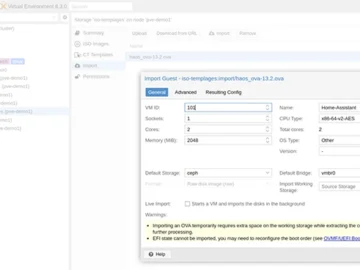
The Proxmox Virtual Environment 8.3 enterprise virtualization solution features management tools and a user-friendly web interface, allowing you to deploy…
Nov 22, 2024Ravie LakshmananArtificial Intelligence / Malware Cybersecurity researchers have discovered two malicious packages uploaded to the Python Package Index…
Artificial Intelligence (AI) is the hottest online commodity right now, and its integration into AI in fuzzing and automated vulnerability…
More than 2,000 Palo Alto Networks firewalls hacked exploiting recently patched zero-days Pierluigi Paganini November 22, 2024 Threat actors already…
A significant cybersecurity risk has been uncovered recently by Censys researchers that unveiled over 145,000 industrial control systems (ICS) devices…
The U.S. Department of Justice (DOJ) announced the seizure of the illicit PopeyeTools platform, a notorious online marketplace for stolen…