In recent years, data breaches and the exposure of sensitive information have become a common occurrence, impacting millions of records…
Nokia has secured a five-year extension of its long-standing agreement to supply routers and switches to Microsoft Azure datacentres worldwide….
Threat actors are actively using a new cash-out technique called “Ghost Tap” to cash out money using credit card information…
US DoJ charges five alleged members of the Scattered Spider cybercrime gang Pierluigi Paganini November 21, 2024 The U.S. Justice…
A design flaw in the Fortinet VPN server’s logging mechanism can be leveraged to conceal the successful verification of credentials…
Multiple decade-old Local Privilege Escalation (LPE) vulnerabilities discovered within the needrestart component installed by default in Ubuntu Server might allow…
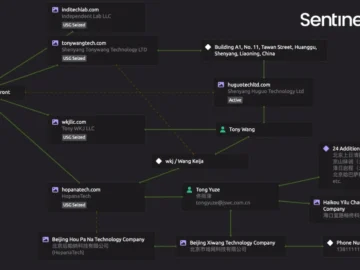
An analysis of the websites belonging to companies that served as a front for getting North Korean IT workers remote…
Renewable energy supplier RWE is tapping into HPE’s private cloud and artificial intelligence (AI) technologies so it can use weather…
21 Nov 4 Hot Startup Storage Vendors To Know In 2024 This week in cybersecurity from the editors at Cybercrime…
Privileged access management (PAM) plays a pivotal role in building a strong security strategy. PAM empowers you to significantly reduce…
Nvidia has continued to see record growth in its datacentre business, driven by the acceleration of artificial intelligence (AI) workloads….
In today’s landscape of advanced phishing attacks, which leverage legitimate domains and sophisticated tactics to evade traditional security measures, it…