Threat actor sells data of over 750,000 patients from a French hospital Pierluigi Paganini November 21, 2024 A threat actor…
Ford is investigating allegations that it suffered a data breach after a threat actor claimed to leak 44,000 customer records…
FrostyGoop, a newly discovered OT-centric malware that exploited Modbus TCP to disrupt critical infrastructure in Ukraine, capable of both internal…
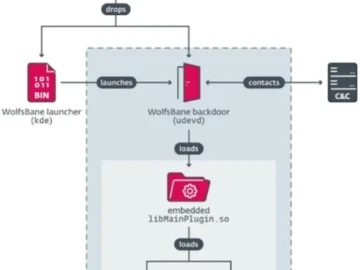
ESET researchers have identified multiple samples of two previously unknown Linux backdoors: WolfsBane and FireWood. The goal of the backdoors…
As many more users are flocking to BlueSky from social media platforms like X/Twitter, so are threat actors. BleepingComputer has…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning regarding two newly discovered vulnerabilities in VMware’s vCenter…
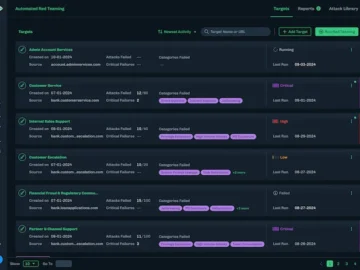
HiddenLayer launched Automated Red Teaming solution for artificial intelligence, a transformative tool that enables security teams to rapidly and thoroughly…
Nov 21, 2024Ravie LakshmananCryptocurrency / Identity Theft Five alleged members of the infamous Scattered Spider cybercrime crew have been indicted…
Federal authorities have unveiled criminal charges against 5 individuals accused of directing a sophisticated phishing scheme targeting employees of companies…
Federal authorities have unsealed charges against five individuals accused of orchestrating sophisticated phishing schemes that targeted employees of companies across…
The Computer Emergency Response Team of Ukraine (CERT-UA), part of the State Service of Special Communications and Information Protection (SSSCIP),…
Kaspersky’s Global Research and Analysis Team (GReAT) has recently uncovered a sophisticated supply chain attack targeting the Python Package Index…