Helldown, a new ransomware group, actively exploits vulnerabilities to breach networks, as since August 2024, they have compromised 28 victims,…
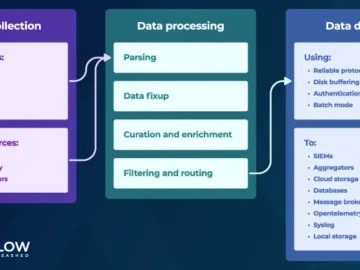
AxoSyslog is a syslog-ng fork, created and maintained by the original creator of syslog-ng, Balazs Scheidler, and his team. “We…
Threat hunters are warning about an updated version of the Python-based NodeStealer that’s now equipped to extract more information from…
Credential phishing remains a formidable threat to organizations worldwide, with malicious actors often relying on tricking individuals into voluntarily revealing…
In recent years, job postings in the software and IT sectors have become commonplace, with companies constantly searching for skilled…
Human-led penetration testing is an essential practice for any organization seeking to proactively address potential attack vectors. However, this indispensable…
In this Help Net Security interview, Brooke Motta, CEO of RAD Security, talks about how cloud-specific threats have evolved and…
Distributed Denial of Service (DDoS) attacks are escalating at an alarming rate, as unveiled in a revelation by Cloudflare researchers…
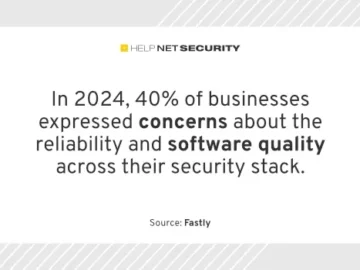
In 2024, businesses reported taking an average of 7.3 months to recover from cybersecurity breaches – 25% longer than expected…
MITRE has released its annual list of the top 25 most dangerous software weaknesses for 2024, highlighting critical vulnerabilities that…
A race condition vulnerability in Apple’s WorkflowKit has been identified, allowing malicious applications to intercept and manipulate shortcuts on macOS…
The University of Newcastle is training future speech pathologists with virtual reality (VR), allowing students to immerse themselves in real-world…