A few years ago I figured out why we’re so creative in the shower Created/Updated: October 26, 2022 Our creativity…
Scottish technology sector trade body ScotlandIS has published its annual survey, suggesting growth in employment is on the cards. The…
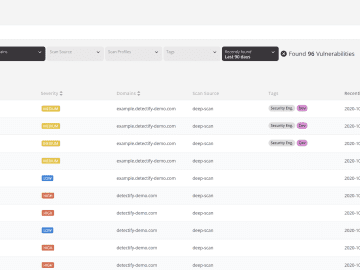
What is vulnerability management? Vulnerability management is the process of continuously identifying, categorizing, and remediating technology system security vulnerabilities. Vulnerability…
BERNINA International hacked! Swiss-based BERNINA International AG, a leading manufacturer of sewing and embroidery machines, has been added to the…
Our Crowdsource ethical hacker community has been busy sending us security updates, including 0-day research. For Asset Monitoring, we now push out tests more…
Apr 26, 2023Ravie LakshmananVirtual Machine / Cybersecurity VMware has released updates to resolve multiple security flaws impacting its Workstation and…
Anonymous Sudan Targets US Hospitals: Within 24 hours of making the disclosure on its Telegram Page, Anonymous Sudan began targeting…
Created/Updated: August 21, 2022 The internet’s gone a bit crazy about Sam Harris supposedly supporting censorship. As in most cases,…
Among the topics they explored included the success of their long-running bug bounty programs in discovering security vulnerabilities, how to…
Artificial intelligence (AI) is a buzzword that has gained significant traction over the past decade. Many experts predict that AI…
Triage is just as important to security teams as it is to hospital workers. Now, you can prioritize and remediate…
Google Authenticator was launched in 2010, which provides additional security for various applications by providing authentication codes for every sign-in….