Trend Micro has disclosed a critical vulnerability in its Deep Security 20 Agent software that could potentially allow attackers to…
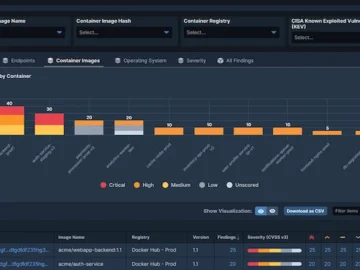
Tanium announced Tanium Cloud Workloads, providing real-time visibility and protection for containerized environments. Through image vulnerability scanning, container run-time inventory,…
A new attack vector utilizing XenoRAT has been uncovered recently, it’s an open-source remote access tool, delivered through Excel XLL…
Businesses are facing increasingly sophisticated threats from ransomware groups, hacktivists, and individual attackers. The 2024 Arctic Wolf Security Operations Report…
Arkose Labs launched Arkose Device ID, a device identification solution that raises the bar in fraud detection by combining precise…
Oracle has issued an urgent security alert regarding a critical vulnerability in its Agile Product Lifecycle Management (PLM) Framework that…
Human beings are without doubt the single biggest cybersecurity threat to organizations. About two-thirds of breaches stem from a simple,…
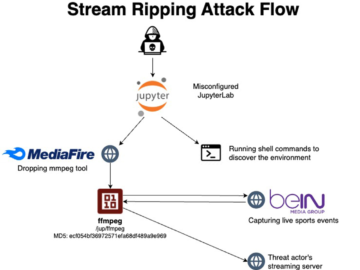
Unsecured JupyterLab and Jupyter Notebooks servers abused for illegal streaming of Sports events Pierluigi Paganini November 20, 2024 Threat actors…
Apple has issued an important security update for macOS Sequoia 15.1.1, addressing several zero-day vulnerabilities that have been actively exploited…
Helldown Ransomware Targets Linux and VMware Server Environments A new variant of ransomware called Helldown, which emerged earlier this year,…
Nov 20, 2024Ravie LakshmananCyber Espionage / Telecom Security A new China-linked cyber espionage group has been attributed as behind a…
A critical security vulnerability has been discovered in Atlassian’s popular version control client, Sourcetree, affecting both Mac and Windows versions….