Human beings are without doubt the single biggest cybersecurity threat to organizations. About two-thirds of breaches stem from a simple,…
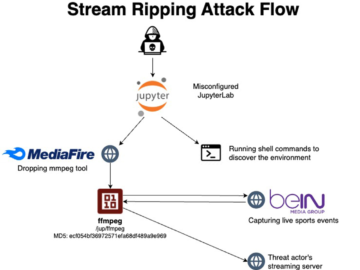
Unsecured JupyterLab and Jupyter Notebooks servers abused for illegal streaming of Sports events Pierluigi Paganini November 20, 2024 Threat actors…
Apple has issued an important security update for macOS Sequoia 15.1.1, addressing several zero-day vulnerabilities that have been actively exploited…
Helldown Ransomware Targets Linux and VMware Server Environments A new variant of ransomware called Helldown, which emerged earlier this year,…
Nov 20, 2024Ravie LakshmananCyber Espionage / Telecom Security A new China-linked cyber espionage group has been attributed as behind a…
A critical security vulnerability has been discovered in Atlassian’s popular version control client, Sourcetree, affecting both Mac and Windows versions….
In today’s digitally connected world, information is at the heart of nearly every transaction, interaction, and decision. While the internet…
Google has rolled out a crucial security update for its Chrome browser, addressing multiple vulnerabilities that could potentially compromise user…
Enterprise copilots and low code/no code capabilities are enabling business users to quickly and easily build new apps and automations…
The ransomware attack on UnitedHealth earlier this year is quickly becoming the healthcare industry’s version of Colonial Pipeline, prompting congressional testimony,…
Nov 20, 2024Ravie LakshmananSoftware Security / Vulnerability Oracle is warning that a high-severity security flaw impacting the Agile Product Lifecycle…
In this Help Net Security interview, Stephanie Domas, CISO at Canonical, discusses common misconceptions about open-source security and how the…