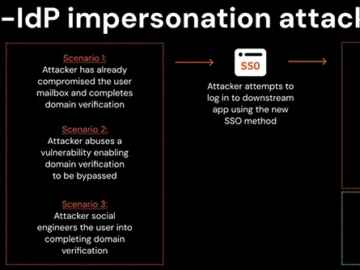
Cross-IdP impersonation – a technique that enables attackers to hijack the single sign-on (SSO) process to gain unauthorized access to…
The Competition and Markets Authority (CMA) has said Alphabet’s partnership with Anthropic does not qualify for investigation under the merger…
China-linked actor’s malware DeepData exploits FortiClient VPN zero-day Pierluigi Paganini November 19, 2024 Chinese threat actors use custom post-exploitation toolkit…
The Ngioweb botnet, which supplies most of the 35,000 bots in the cybercriminal NSOCKS proxy service, is being disrupted as…
In recent years, online users have increasingly found themselves the target of spam emails. These unwanted messages flood inboxes after…
Nov 19, 2024Ravie LakshmananCloud Security / Piracy Malicious actors are exploiting misconfigured JupyterLab and Jupyter Notebooks to conduct stream ripping…
Cyber resilience has dominated headlines this year as major outages impacting people, businesses, and public services hit the headlines. But…
Microsoft is working on a new Windows “Quick Machine Recovery” feature that will allow IT administrators to use Windows Update…
A large social media campaign was launched to promote a free Artificial Intelligence (AI) video editor. If the “free” part…
The malware known as Ngioweb has been used to fuel a notorious residential proxy service called NSOCKS, as well as…
Recent years have seen a general cost-cutting in organisations caused by economic pressures. Many organisations have seen a fall in…
19 Nov Rethinking Cybersecurity From Cost Center To Value Driver This week in cybersecurity from the editors at Cybercrime Magazine…