Detectify is helping tech organizations bring safer web products to market by providing crowdsourced, cloud-based, continuous web app security. Here’s…
Exploring the intersection of security, technology, and society—and what might be coming next… Standard Web Edition | November 28, 2022…
A guide to expertly tackling seemingly complicated problems that you’d rather never tackle in the first place. What if I…
Like triaging in a hospital emergency room, security issues must be diagnosed and handled by an expert as soon as…
Identity theft continues to be a major cause of concern as hackers are finding new ways to exploit the information….
We’re going to highlight the Top high severity CVEs found by Detectify. Thanks to the Crowdsource global community of handpicked…
If you’re reading this you already know the internet is on fire over the new GPTChatBot from OpenAI. There are…
Apr 22, 2023Ravie LakshmananPatch Management / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added three security…
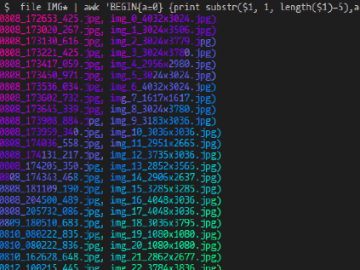
How to batch rename images with custom values using file, awk, and rename – in rainbow colors! The most recent…
Apr 22, 2023Ravie LakshmananSupply Chain / Cyber Threat Lazarus, the prolific North Korean hacking group behind the cascading supply chain…
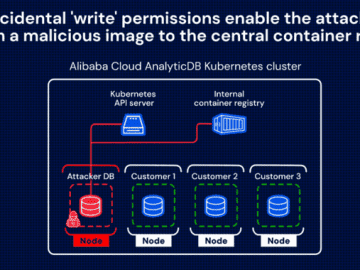
Two new critical flaws have been found in Alibaba Cloud’s popular services, ApsaraDB and AnalyticDB. Both of them were in…
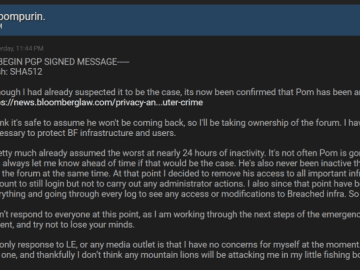
After the arrest of the former admin of the BreachForums, Pompompurin, the succeeding administrator Baphomet has gotten into a game…