Researchers discovered a novel approach employed by the threat actor to conceal codes using Extended Attributes to avoid detection in…
14 Nov Cybersecurity in Crisis: How to Combat the $10.5 Trillion Cybercrime Surge This week in cybersecurity from the editors…
MPs have debated police use of live facial recognition (LFR) for the first time, with a consensus emerging on the…
Stealers are designed to be stealthy primarily to avoid detection by AV tools and to remain hidden from the user….
Group-IB has uncovered Lazarus group’s stealthy new trojan and technique of hiding malicious code in extended attributes on macOS. Learn…
Despite the countermeasures some services are taking against well-known ad blockers, lots of people now use one. This is no…
A new and sophisticated malware threat has emerged in the cybersecurity landscape, targeting unsuspecting users and potentially compromising their privacy…
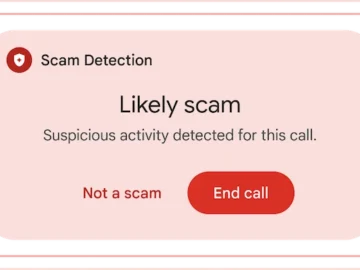
Google has announced new security features for Android that provide real-time protection against scams and harmful apps. These features, powered…
A 33-year-old Nigerian man living in the UK and his co-conspirators defrauded over 400 would-be home buyers in the US….
The Cybersecurity and Infrastructure Security Agency (CISA) has recently issued a series of security advisories, shedding light on several critical…
After months of news reports that Chinese threat actors have breached the networks of US telecommunications and internet service providers,…
Ransomware isn’t just a buzzword; it’s one of the most dreaded challenges businesses face in this increasingly digitized world. Ransomware…