Let’s be honest—nobody likes thinking about worst-case scenarios. But in today’s digital terrain, cyberattacks are less of an “if” and…
If you’re looking to make some extra cash or to start a business, you should consider online reselling. Online reselling…
Kaspersky, the cybersecurity firm originally based in Russia, has uncovered a troubling trend where cybercriminal groups are teaming up to…
Red Hat has announced its intention to acquire Neural Magic, the lead developer behind the open source vLLM project. The…
There is no doubt that attackers have shifted their attention to APIs. Wallarm’s API ThreatStats research identifies that 70% of…
A sophisticated malware campaign targeting macOS devices, believed to be orchestrated by North Korean state-sponsored or APT hackers. The malicious…
Malware sandboxes offer a safe and controlled environment to analyze potentially harmful software and URLs. However, not all sandboxes incorporate…
Keeping track of who has access and managing their permissions has gotten a lot more complicated because there are so…
Bitdefender has released a free decryptor for ShrinkLocker ransomware, which exploits Windows BitLocker to encrypt systems. Discover all about the…
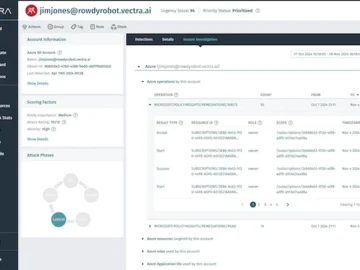
Vectra AI announced the extension of the Vectra AI Platform to include comprehensive coverage for customers’ Microsoft Azure environments. With…
Small businesses and startups are known to face some extra challenges when it comes to cybersecurity. Because they don’t have…
Romanian cybersecurity company Bitdefender has released a free decryptor to help victims recover data encrypted using the ShrinkLocker ransomware. The…