Armorblox has released its newest product, Graymail and Recon Attack Protection, developed to decrease the time security teams spend managing…
A joint advisory about a Cisco vulnerability by several US and UK agencies gives us a peek inside the minds…
How to set up an interactive checklist using a Git pre-commit hook script. What’s that, you say? You’ve become tired…
We take a look at a story involving the FTC going head to head with a payment processor caught up…
We learned some remarkable new details this week about the recent supply-chain attack on VoIP software provider 3CX. The lengthy,…
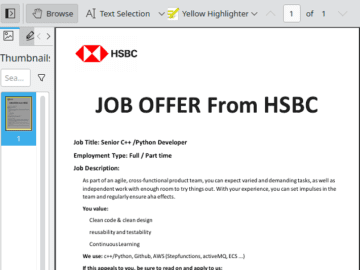
QBot has resurfaced with a new tactic involving a reply-chain phishing email, a fake PDF, and the likely promise of…
Hackers! We have made it to Las Vegas! We are here for a live hacking event (LHE). All live hacking…
Cisco Industrial Network Director (IND) is an important tool for managing industrial networks, particularly in settings that need high-security standards….
#1 in Endpoint Protection, #1 ROI for EDR, #1 for EDR implementation. Navigating the world of endpoint security is challenging,…
Detectify is driving the future of internet security with automation and crowdsourcing hacker research. It’s focused on helping companies detect…
Exploring the intersection of security, technology, and society—and what might be coming next… Standard Web Edition | Ep. 362 |…
Some thoughts inspired by International Women’s Day, Grace Hopper, and making contributions to the world of tech. It’s International Women’s…