Some companies have been using AI as a data analytics tool for years, but most companies are now rushing to…
As Australian households continue to embrace high-speed internet, a reliable and fast Wi-Fi network has become essential, especially for large…
NSW Department of Customer Service is looking to the multilingual capabilities of generative AI for more accessible and inclusive public…
An ongoing phishing scam is abusing Google Calendar invites and Google Drawings pages to steal credentials while bypassing spam filters….
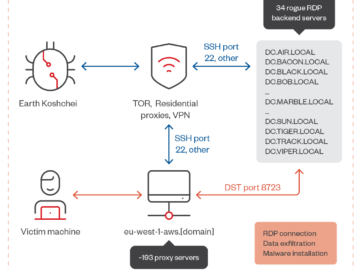
Russia-linked APT29 group used red team tools in rogue RDP attacks Pierluigi Paganini December 18, 2024 Russia-linked APT29 group uses…
The Russian hacking group tracked as APT29 (aka “Midnight Blizzard”) is using a network of 193 remote desktop protocol proxy servers…
Stay alert to crypto scams with our guide to 2024’s top threats, including phishing, malware, Ponzi schemes, and fake wallets….
Ukrainian national Mark Sokolovsky was sentenced today to five years in prison for his involvement in the Raccoon Stealer malware…
UNSW is exploring how to integrate ChatGPT into its digital ecosystem through a 12-month pilot. The university has rolled out…
UNSW is exploring how to integrate ChatGPT into its digital ecosystem through a 12-month pilot. The university has rolled out…
US authorities are considering a ban on China’s TP-Link Technology Co over potential national security concerns after its home internet…
Threat actors are attempting to exploit Apache Struts vulnerability CVE-2024-53677 Pierluigi Paganini December 18, 2024 Researchers warn that threat actors…