Microsoft has confirmed that last month’s Windows security updates are breaking SSH connections on some Windows 11 22H2 and 23H2…
Cybercriminals have launched a large-scale phishing attack using a new variant of Rhadamanthys Stealer, dubbed CopyRh(ight)adamantys, which targets individuals and…
Google has quietly updated the description of one of Chrome’s security features, “Enchaned protection,” to confirm that it will be…
North Korean threat actors, likely associated with BlueNoroff, have launched multi-stage malware attacks targeting cryptocurrency businesses, expanding their toolkit to…
As the winter season kicks in, scammers are not missing the chance to target senior British residents with bogus “winter…
As part of its efforts to add AI everywhere, Microsoft is now bringing AI features to the popular Paint and…
The Federal Bureau of Investigation (FBI) is urging police departments and governments worldwide to beef up security around their email…
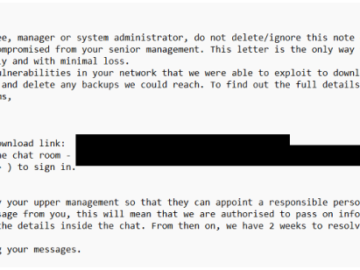
Veeam Backup & Replication exploit reused in new Frag ransomware attack Pierluigi Paganini November 09, 2024 A critical flaw, tracked…
This article explains the inner workings of the Remcos RAT, a dangerous malware that uses advanced techniques to infect Windows…
Cybersecurity tools and technologies are continuously being developed and refined to keep pace with the growing threat landscape. One tool…
Maybe you already heard, but Donald Trump will be president of the United States again. The far-right is celebrating by…
Nov 09, 2024Ravie LakshmananVulnerability / Network Security Palo Alto Networks on Friday issued an informational advisory urging customers to ensure…